The evolution of cryptography part 2: The dawn of the digital age

This is the second in our series of articles looking back at the evolution of cryptography – from simple displacement systems used to conceal messages, to elaborate digital protocols that have facilitated a financial revolution.
In part 1 of this series, we looked at how cryptography in early civilisations was dominated by the use of monoalphabetic substitution ciphers. These were effectively rendered redundant in the ninth century – or, at least, made far easier to solve – by Al-Kindi’s work around frequency analysis.
Al-Kindi’s work forced cryptographers to develop new techniques to stay ahead of codebreakers. These developments laid the foundations for the digital age, and many of the principles are still being applied today.
The Polyalphabetic Cipher
Historically, cryptographers in Europe lagged behind their Arabic counterparts. This began to change around the 13th century, driven primarily by the rise of city states in Italy, such as Venice and Florence. The rivalries that emerged between these states caused a sharp increase in the volume of diplomatic messages being sent across the country. Their sensitive nature meant security was paramount, and increasingly complex ciphers had to be developed to protect the content.
In 1467, Leon Battista Alberti was asked to develop a system for the papal court. He devised the polyalphabetic cipher – two copper discs, each of them with a different alphabet inscribed on.
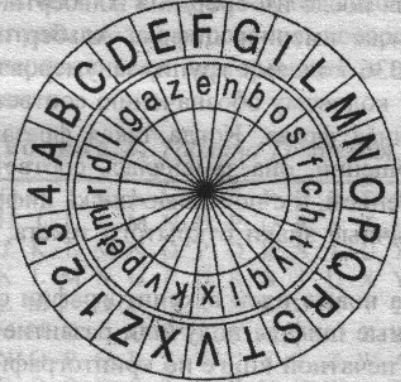
The polyalphabetic cipher is a simple but incredibly effective method of encryption. On one disc is the alphabet in which the original message is written. On the second is an entirely different alphabet that the message appears in after it has been encoded. The reader has to know the alphabet in which the message was originally written or it will be impossible to solve, even by frequency analysis.
Furthermore, after every few words, the discs are rotated to change the encryption logic. This further limits the use of frequency analysis to crack the cipher. It also allows the sender to change alphabets at arbitrary spots in the encryption process. The signal of an alphabet change still has to be agreed upon in advance between the sender and receiver, though. Therefore, this is still a symmetrical method of encryption.
The use of cipher discs remained popular up until the twentieth century. During this time, they were iterated upon and improved by a number of leading cryptographers. Among them was German abbot, Johannes Trithemius, who invented the tabula recta in 1518.
The tabula recta is a square table of alphabets.Each row is shifted once to the left to create 26 different Caesar ciphers. The plaintext letters are on the left-vertical row of the tabula recta. You then take the corresponding letter from your keyword, and find it at the top-horizontal row of the table. Where these two lines cross in the table is the ciphertext letter.

The tabula recta was further developed by Giovan Battista Bellaso, who added keywords for additional security. The Vigenère cipher, as it became known, codified popular or regularly-used words using a single symbol to represent the whole word. This made it even more difficult to solve.
In Vigenère’s cipher, the encryption key is repeated multiple times across the entire message. The ciphertext is then produced by adding the message character with the key character modulo 26. This means Vigenere’s cipher is easily broken. The use of a repeating key means that, if a cryptanalyst is able uncover the length of the key, they can treat the ciphertext as a number of interwoven Caesar Ciphers and break them individually. However, Vigenere’s cipher is still important because it introduced the idea of encryption keys to cryptography. These have since become a mainstay in cryptography and blockchain technology.
The Vigenère Cipher actually remained uncracked for over 200 years. It wasn’t until 1854 that Charles Babbage, the inventor of the digital programmable computer, discovered that enciphering the plaintext with a keyword renders the ciphertext subject to modular arithmetic. This meant that popular or regularly-used words could be codified using a single symbol to represent the whole word.
Enter electricity
By the start of the 19th century, the world had gone electric. This gave cryptography a fresh shot in the arm, enabling a new breed of cipher machines.
One of the first such machines was designed by Edward Hebern. He created an electro-mechanical contraption that became known as the Hebern rotor machine. The machine was built by connecting the mechanical parts of a standard typewriter with the electrical parts of an electric typewriter, and putting a scrambling unit in the middle. It used a single rotor, in which the secret key is embedded in a rotating disc. The key encoded a substitution table. Every time a key was pressed on the keyboard, the output would be the ciphertext. This also rotated the disc by one notch and a different table would then be used for the next plaintext character.
The Hebern rotor machine was eventually broken by using letter frequencies. It is, however, the first example of a class of machines known as rotor machines – the most famous of which was the Enigma machine. Invented by German engineer Arthur Scherbius in 1918, the Enigma was a defining moment in modern cryptography. And cracking it was a defining moment in the history of the world.
Enigma
The Enigma Machine might look like an ordinary typewriter, but the reality is far more complex.

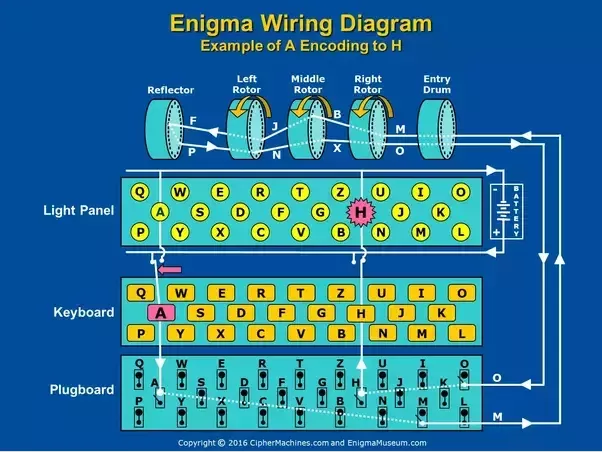
The basic design of Scherbius’s invention is similar to Hebern’s design in many ways, but with some important additions: the plugboard and extra rotors in the scrambling unit.
To work the Enigma machine, you press a key on the keyboard. This generates an electric signal, which is then sent through to the plugboard. The plugboard consists of 26 pairs of sockets. It swaps pairs of letters before they enter the scrambling unit. For example, entering the letter B sends the electrical signal through the scrambling unit that would have otherwise been the path for the letter A, and vice versa.
The signal is then sent to the scrambling unit. This consists of three rotors moving at different speeds, each with a gauge displaying numbers from 1 to 26. The electric signal passes through them, changing the number in the gauge next to it as they rotate. This means there are more than 17,000 different combinations before the encryption process repeats itself. To improve it even further, Scherbius made the scramblers removable and interchangeable, which increases security by a factor of 6. The signal then goes through a reflector, which sends the signal back again, before finally lighting up one of the output letters and producing your ciphertext.
It was World War II when Enigma really gained its fame. For additional security, the German military services usually double-encrypted their messages by first substituting original text with code words and then enciphering the encoded text. But the Germans were overconfident about its security and used it to encode almost all of their secret messages. They used it so much, in fact, that once it was cracked, the impact on their operations was devastating.
Cracking the code the dawn of the digital age
During the 1930s, Poland’s Marian Rejewski built the first “Bombe” – an electromechanical machine that copied Enigma’s process to brute-force test potential encryption keys until it got the right one. When Germany invaded Poland in September 1939, the Polish shared their findings with the UK. Their work allowed the cryptanalysts at Bletchley Park, such as Alan Turing, to finally crack the Enigma ciphers.
British cryptanalysts at Bletchley Park also managed to break the Lorentz cipher, which was arguably at least equal in significance to Enigma as Hitler used the Lorentz cipher to communicate with his generals. This would also have long standing repercussions for tech.
Lorentz was another electromechanical machine, though in this case it used a teleprinter. Teleprinters are based on the 32-symbol Baudot code, rather than the alphabet. The Baudot code output consists of five channels, each of which is a stream of bits which can be represented as no-hole or hole, 0 or 1, dot or cross. In order to mechanise the codebreakers’ breakthrough, Max Newman designed the very first programmable electronic computer, which Tommy Flowers built it in 1943. They named the computer Colossus.
The computer has arrived, bringing with it the ability to crack codes of unprecedented velocity faster than ever before. From this came the creation of blockchain and cryptocurrency.
Keep reading…
Top crypto trends to watch out for in 2020
 Discover
Discover Help Centre
Help Centre Status
Status Company
Company Careers
Careers Press
Press